Bitlocker For Windows 10 Home
- Bitlocker Download For Windows 10 Home Edition
- Win 10 Home Bitlocker
- Download Windows Bitlocker For Free
- Download Bitlocker For Windows 10
- Enable Bitlocker For Windows 10 Home
- Bitlocker For Windows 10 Home Download 64 Bit
This tutorial contains instructions o how to disable Bitlocker Protection and Drive encryption in Windows 10. As you may know, the BitLocker encryption feature which is available in Windows 10 pro and enterprise versions, can help you to protect your PC contents from unauthorized access. But sometimes there is the need to disable the Bitlocker on Windows 10, so in this guide you can find how to do that.
If your computer is protected with BitLocker, then when you start the system, you will be prompted to connect the USB drive that you used during BitLocker activation or to enter your BitLocker password to unlock the drive C: in order to continue booting. If you do not have any of these, then press ESC to enter your BitLocker recovery key. *
Configure BitLocker drive encryption on Windows 10. In order to enable And configure BitLocker drive encryption feature on Windows 10. First click on Start menu search and type control pane. Here on control panel click on System And Security. Here you will see the option BitLocker Drive Encryption Click on it. This will open the BitLocker Drive Encryption Window. If you are running Windows 10 on an older computer without the Trusted Platform Module chip (TPM 1.2), you might not be able to setup BitLocker. Please review troubleshooting steps further down in.
* Notes:
1. If the Bitlocker Recovery Key or Password is not accepted at system startup then try to unlock and decrypt the hard drive to another Windows 10 computer or try to : Unlock and Decrypt the Protected Drive in the Windows Recovery Environment (WinRE).
2. If you Cannot Unlock the Drive (e.g. If don't own the BitLocker Recovery Key or because the BitLocker key is not accepted) and you want to remove the BitLocker encryption in order to use the protected drive again, then read this tutorial: How to Remove BitLocker Protection from a Drive Without the BitLocker Recovery key or Password.
Bitlocker Download For Windows 10 Home Edition
After booting to Windows then follow the instructions below to disable the bitlocker protection and to decrypt the drive.
How to Turn Off BitLocker Protection and Decrypt a Bitlocker Encrypted Drive in Windows 10.
In order to turn off the Bitlocker protection, you must have the Bitlocker password or the bitlocker recovery key in order to unlock the drive first and then to decrypt the drive.
The Bitlocker recovery key is a 48-digit number key and can be found at following locations:
Win 10 Home Bitlocker
- On a printout you saved, when you enabled Bitlocker.
- On a USB drive you used, during the Bitlocker activation to save the Bitlocker recover key.
- At the Microsoft Account Recovery Keys, by using the MS account you using to login to your device, or you have added to the device in order to download apps from Microsoft Store, or to activate MS Office or for email.
- On your Azure Account for work PC's that login with an Azure Active Directory account.
Once you find the Bitlocker recovery key or the bitlocker password, then proceed to unlock the Bitlocker encrypted drive and to remove the Bitlocker encryption by using one of the following ways:
Method 1. How to Turn Off Bitlocker Protection in Windows 10 GUI.
To disable the protection on your System Drive C:
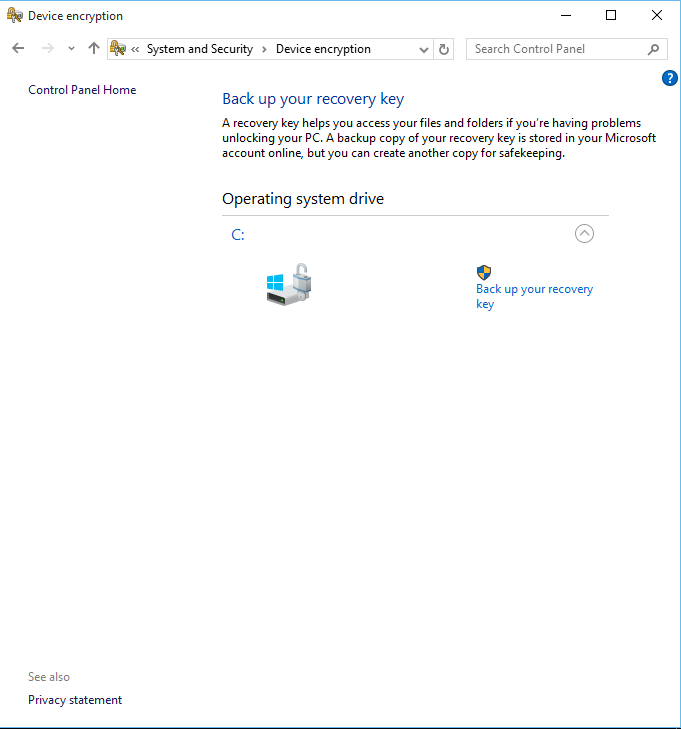
1. Navigate to Windows Control Panel -> System and Security and then click Bit Locker Drive Encryption.
2. Next to the operating system drive C:, click Turn On BitLocker. *
3. After Turning Off the Bitlocker, then click at the Bitlocker icon in the taskbar to view the decryption process.
To disable the protection on any other BitLocker protected drive from Windows GUI:
1. Open Windows Explorer and then double click on the locked drive.
2. Enter the Bitlocker password or click More Options to enter the Bitlocker Recovery key, in order to unlock the drive.
2. After unlocking the drive, then navigate to Control Panel -> System and Security -> Bit Locker Drive Encryption and after selecting the drive click Turn off BitLocker to decrypt the drive. (see the screenshots above)
Method 2. How to Turn OFF BitLocker Protection & Decrypt a Bitlocker Encrypted Drive from PowerShell in Windows 10.
1. Open PowerShell as Administrator. To do that:
Download Windows Bitlocker For Free
- At Cortana's search box, type powershell
- Right click on Windows PowerShell result and select Run as administrator.
2. Then check the encryption status of each drive on your computer, by typing this command:
- manage-bde -status
3. Note in which drive letter the Lock Status shows Locked, and then proceed to unlock that drive, by typing this command: *
- manage-bde -unlock drive-letter: -rp BitLocker-recovery-key
Download Bitlocker For Windows 10
* e.g.: If you want to unlock the drive 'D:' and the bitlocker recovery key is: '123456-123456-123456-123456-123456-123456' then type:
- manage-bde -unlock D: -rp 123456-123456-123456-123456-123456-123456
* Note: If you know the Bitlocker password then give this command:
- manage-bde -unlock drive-letter: -pw BitLocker-Password
* e.g.: If you want to unlock the drive 'D:' and the BitLocker password is: '123qwerty' then type: *
- manage-bde -unlock D: -password 123qwerty
4. Then disable the bitlocker encryption and decrypt the encrypted drive, by using one of the following commands:
- Disable-BitLocker -MountPoint 'drive-letter:'
- manage-bde -off drive-letter:
* e.g.: If you want to disable the bitlocker encryption on drive 'D:', then type:
- Disable-BitLocker -MountPoint 'D:'
OR type…
- manage-bde –off D:
5. When the decryption process is completed, proceed to check again the encryption status by giving this command:
- manage-bde -status
6. If the 'Lock Status' shows Unlocked and the 'Conversion Status' shows Fully Decrypted, you're done!
That's all folks! Did it work for you?
Please leave a comment in the comment section below or even better: like and share this blog post in the social networks to help spread the word about this problem.
Applies to
- Windows 10
Enable Bitlocker For Windows 10 Home
This topic provides a high-level overview of BitLocker, including a list of system requirements, practical applications, and deprecated features.
BitLocker overview
BitLocker Drive Encryption is a data protection feature that integrates with the operating system and addresses the threats of data theft or exposure from lost, stolen, or inappropriately decommissioned computers.
BitLocker provides the most protection when used with a Trusted Platform Module (TPM) version 1.2 or later. The TPM is a hardware component installed in many newer computers by the computer manufacturers. It works with BitLocker to help protect user data and to ensure that a computer has not been tampered with while the system was offline.
On computers that do not have a TPM version 1.2 or later, you can still use BitLocker to encrypt the Windows operating system drive. However, this implementation will require the user to insert a USB startup key to start the computer or resume from hibernation. Starting with Windows 8, you can use an operating system volume password to protect the operating system volume on a computer without TPM. Both options do not provide the pre-startup system integrity verification offered by BitLocker with a TPM.
In addition to the TPM, BitLocker offers the option to lock the normal startup process until the user supplies a personal identification number (PIN) or inserts a removable device, such as a USB flash drive, that contains a startup key. These additional security measures provide multifactor authentication and assurance that the computer will not start or resume from hibernation until the correct PIN or startup key is presented.
Practical applications
Data on a lost or stolen computer is vulnerable to unauthorized access, either by running a software-attack tool against it or by transferring the computer's hard disk to a different computer. BitLocker helps mitigate unauthorized data access by enhancing file and system protections. BitLocker also helps render data inaccessible when BitLocker-protected computers are decommissioned or recycled.
There are two additional tools in the Remote Server Administration Tools, which you can use to manage BitLocker.
BitLocker Recovery Password Viewer. The BitLocker Recovery Password Viewer enables you to locate and view BitLocker Drive Encryption recovery passwords that have been backed up to Active Directory Domain Services (AD DS). You can use this tool to help recover data that is stored on a drive that has been encrypted by using BitLocker. The BitLocker Recovery Password Viewer tool is an extension for the Active Directory Users and Computers Microsoft Management Console (MMC) snap-in.By using this tool, you can examine a computer object's Properties dialog box to view the corresponding BitLocker recovery passwords. Additionally, you can right-click a domain container and then search for a BitLocker recovery password across all the domains in the Active Directory forest. To view recovery passwords, you must be a domain administrator, or you must have been delegated permissions by a domain administrator.
BitLocker Drive Encryption Tools. BitLocker Drive Encryption Tools include the command-line tools, manage-bde and repair-bde, and the BitLocker cmdlets for Windows PowerShell. Both manage-bde and the BitLocker cmdlets can be used to perform any task that can be accomplished through theBitLocker control panel, and they are appropriate to use for automated deployments and other scripting scenarios. Repair-bde is provided for disaster recovery scenarios in which a BitLocker protected drive cannot be unlocked normally or by using the recovery console.
New and changed functionality
To find out what's new in BitLocker for Windows 10, such as support for the XTS-AES encryption algorithm, see the BitLocker section in 'What's new in Windows 10.'
Autotune software for mac. Setup File Name: Antares Auto-Tune 7.6.8.zip. Setup Type: Offline Installer / Full Standalone Setup.
System requirements
BitLocker has the following hardware requirements:
For BitLocker to use the system integrity check provided by a Trusted Platform Module (TPM), the computer must have TPM 1.2 or later. If your computer does not have a TPM, enabling BitLocker requires that you save a startup key on a removable device, such as a USB flash drive.
A computer with a TPM must also have a Trusted Computing Group (TCG)-compliant BIOS or UEFI firmware. The BIOS or UEFI firmware establishes a chain of trust for the pre-operating system startup, and it must include support for TCG-specified Static Root of Trust Measurement. A computer without a TPM does not require TCG-compliant firmware.
The system BIOS or UEFI firmware (for TPM and non-TPM computers) must support the USB mass storage device class, including reading small files on a USB flash drive in the pre-operating system environment.
Important
From Windows 7, you can encrypt an OS drive without a TPM and USB flash drive. For this procedure, see Tip of the Day: Bitlocker without TPM or USB.
Note
Bitlocker For Windows 10 Home Download 64 Bit
TPM 2.0 is not supported in Legacy and CSM Modes of the BIOS. Devices with TPM 2.0 must have their BIOS mode configured as Native UEFI only. The Legacy and Compatibility Support Module (CSM) options must be disabled. For added security Enable the Secure Boot feature.
Installed Operating System on hardware in legacy mode will stop the OS from booting when the BIOS mode is changed to UEFI. Use the tool MBR2GPT before changing the BIOS mode which will prepare the OS and the disk to support UEFI.
The hard disk must be partitioned with at least two drives:
- The operating system drive (or boot drive) contains the operating system and its support files. It must be formatted with the NTFS file system.
- The system drive contains the files that are needed to load Windows after the firmware has prepared the system hardware. BitLocker is not enabled on this drive. For BitLocker to work, the system drive must not be encrypted, must differ from the operating system drive, and must be formatted with the FAT32 file system on computers that use UEFI-based firmware or with the NTFS file system on computers that use BIOS firmware. We recommend that system drive be approximately 350 MB in size. After BitLocker is turned on it should have approximately 250 MB of free space.
When installed on a new computer, Windows will automatically create the partitions that are required for BitLocker.
When installing the BitLocker optional component on a server you will also need to install the Enhanced Storage feature, which is used to support hardware encrypted drives.
In this section
| Topic | Description |
|---|---|
| Overview of BitLocker Device Encryption in Windows 10 | This topic for the IT professional provides an overview of the ways that BitLocker Device Encryption can help protect data on devices running Windows 10. |
| BitLocker frequently asked questions (FAQ) | This topic for the IT professional answers frequently asked questions concerning the requirements to use, upgrade, deploy and administer, and key management policies for BitLocker. |
| Prepare your organization for BitLocker: Planning and policies | This topic for the IT professional explains how can you plan your BitLocker deployment. |
| BitLocker basic deployment | This topic for the IT professional explains how BitLocker features can be used to protect your data through drive encryption. |
| BitLocker: How to deploy on Windows Server | This topic for the IT professional explains how to deploy BitLocker on Windows Server. |
| BitLocker: How to enable Network Unlock | This topic for the IT professional describes how BitLocker Network Unlock works and how to configure it. |
| BitLocker: Use BitLocker Drive Encryption Tools to manage BitLocker | This topic for the IT professional describes how to use tools to manage BitLocker. |
| BitLocker: Use BitLocker Recovery Password Viewer | This topic for the IT professional describes how to use the BitLocker Recovery Password Viewer. |
| BitLocker Group Policy settings | This topic for IT professionals describes the function, location, and effect of each Group Policy setting that is used to manage BitLocker. |
| BCD settings and BitLocker | This topic for IT professionals describes the BCD settings that are used by BitLocker. |
| BitLocker Recovery Guide | This topic for IT professionals describes how to recover BitLocker keys from AD DS. |
| Protect BitLocker from pre-boot attacks | This detailed guide will help you understand the circumstances under which the use of pre-boot authentication is recommended for devices running Windows 10, Windows 8.1, Windows 8, or Windows 7; and when it can be safely omitted from a device’s configuration. |
| Protecting cluster shared volumes and storage area networks with BitLocker | This topic for IT pros describes how to protect CSVs and SANs with BitLocker. |
| Enabling Secure Boot and BitLocker Device Encryption on Windows 10 IoT Core | This topic covers how to use BitLocker with Windows 10 IoT Core |